What does cyber security do?
Cyber security works just like normal offline security, i.e. its purpose is to keep users and their computer systems safe. In the real world, you might be happy with a video doorbell and locks on all the windows, but online, things aren’t as easy as that. Online fraudsters can gain access to your information in a number of ways. They might even convince you to send it to them of your own free will, simply because you don’t realise you are being scammed. The Internet can be a scary place and it can be dangerous to go alone, that’s why you need to make sure some solid security has your back.
What does cyber security protect against?
Cyber crimes are motivated by money and that has led to hundreds of different methods of getting you to part with yours. In some cases, it can be as simple as targeting your bank account, in others, they try to take your ID. In some truly scary situations, cyber criminals may lay siege to your whole computer, almost like they’re right there in your home with you.
Types of cyber attack
Here are the most common types of cyber attack for you to be aware of:
Malware
Malware is malicious software that attackers purposefully install on your computer. Malware often finds its way onto computers by masquerading as innocent email attachments or as a fake button on websites, allowing it to bypass network security. Malware can transmit your personal data (known as spyware), install further malicious software or simply shut down your operating system altogether. To ensure computer security, you should only download files you know are safe.
Ransomware
Ransomware is a form of malware that encrypts all your files. You won’t know you are downloading ransomware. Often it will arrive in your inbox, named as an innocent file from an innocent-sounding sender. Once you open it, your files will be inaccessible, and in order to gain control back, you will have to pay a ransom. You can guarantee, of course, that even after paying, you’ll only be left with a lighter wallet and the wish that you could just rewind.
Phishing
Phishing is when a scammer poses as a trustworthy source. A phishing attack can take place in the form of email, social media message or even phone call. You will receive a message, often from someone claiming to be from your bank, asking for you to confirm your details, share a credit card number or make a money transfer. They will then use your details to gain unauthorised access to your accounts. Sometimes, phishing messages will even bluff and say that in order to ensure your account is safe from scammers, you should click on a certain link or share your bank account details. Never, ever respond to these requests. Information security is top priority for banks, so they definitely won't email out of the blue asking for information. If you are concerned about a message, don't act on it, but call the bank to check if it is legitimate.
Denial of Service (DDoS)
A DDoS attack is when your network or server is overwhelmed with a flood of Internet traffic. With so much traffic using up your bandwidth, you are not able to use the network for legitimate needs. This type of attack is most often used to target the websites of businesses and organisations. The end goal here is not necessarily money (at least not for the scammer) but to deny you customers and viewers. It’s essentially the same as an online picket line. DDoS attacks have been, arguably, used ‘for good’ to stop hate groups from gaining traction online by blocking access to their sites.
Man in the middle attack
This is when cyber attackers place themselves between you and another party and assumes the appearance of you both. For example, if you are talking to a friend and want to pay them back for something, you send your account number. Your friend sees the message and makes the payment. You see the message saying your friend has paid. Neither you nor your friend will see any evidence that there is a scammer in the middle, as the scammer is posing as both of you. You never receive the money, though, as the scammer has replaced your message and account number with their own. This identity theft could potentially go on for days, or even weeks, before anyone realises something is amiss.
How can I protect myself from a cybersecurity attack?
Using cyber security will help detect any suspicious activity and keep it at bay. There are as many security solutions as there are types of attack, so you may need multiple cyber security tools to keep you, your business or your family secure.
Types of cyber security
Encryption
Encryption – when used correctly and not in ransomware – is a great thing for your security. A program or service that uses encryption will take your messages or files and makes them into a code that make their true meaning impossible to read. That means even if there is someone in the middle of your communications, they won’t be able to see anything. Encryption is a security essential you should look out for when using any service to transfer files.
VPNs
VPNs have multiple uses, such as enabling remote network accessibility, but they are also fantastic defence from cyber attacks. VPNs disguise your IP address, that is the address that serves as your unique ID online, a bit like your real address. By masking this, any would-be scammers are unable to know your location or network. For example, you may be based in the United States, but a VPN can mask your IP address with a European one.
Authentication
A little less complicated. Authentication is about making sure you are who you say you are, so no scammer can log into your accounts. Usually, this is done simply by password, but many services now insist on two-step authentication and you should absolutely agree to it. Two-step authentication means double the security, and, as it very often means you have to log in with a code sent to your email or phone, it’s unlikely a hacker will be able to gain access to all these channels.
You should look out for this sort of security when you have any data stored online like shared files or your inbox. Another authentication security solution is SSO or single sign on. This allows you to only log in once to get access to multiple systems. While that may sound like it’s a short-cut to being scammed across multiple accounts, the reverse is true. By having a single sign in, you don’t have a unique login and multiple strong passwords for every account you use, that means less sensitive data and less chance of it being stolen.
SIEM
SIEM, short for Security Information and Event Management, is a form of security that works in real time. SIEM solutions are sold in the form of software or services and monitor activity of a business so that any anomalies can be instantly alerted and prevented. Depending on your program or service, SIEM can also help compile compliance reports and assist in disaster recovery.
Antivirus and firewalls
The simplest security measures you can install yourself, these should 100% be present on your laptop and mobile devices. Firewall protection and anti-viruses can help stop malicious programs even if you have clicked download, detecting cyber security threats and deleting them on sight or moving them to a secure folder.
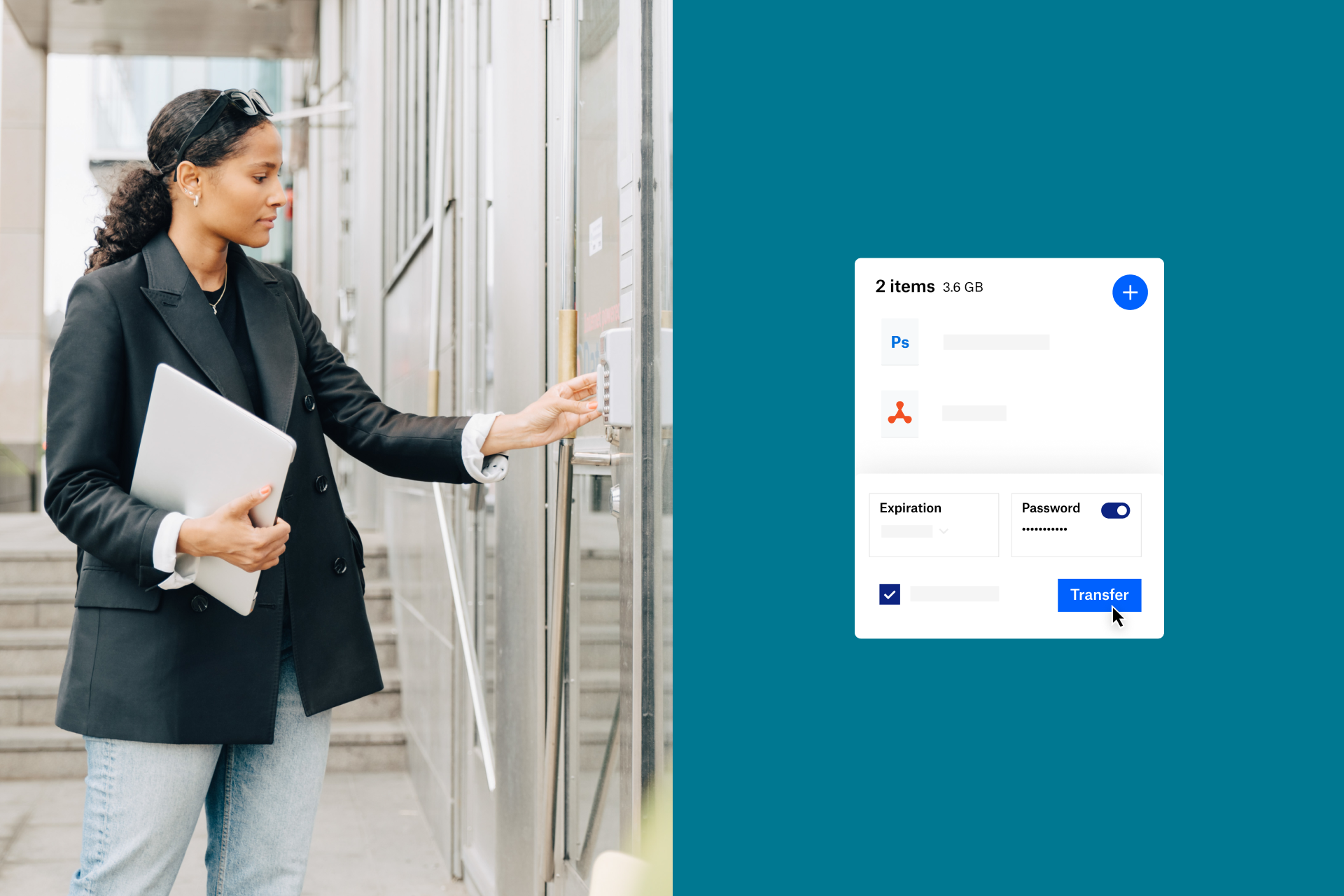
How Dropbox keeps you secure
Protecting sensitive information and documents is crucial to any business, but it’s especially important when you’re dealing with legal files that help transform lives. IRAP, a not-for-profit, works with lawyers around the world to get justice for refugees facing persecution. With Dropbox’s help and data protection, they can do so knowing their files are safe. “We feel very comfortable putting our clients’ information on Dropbox Business because we can control who has access, and for how long”, explains IRAP’s Deputy Legal Director Lara Finkbeiner.
At Dropbox, we are security professionals, making sure your data and folders are always secure. We use multi-layer protection and can support your compliance strategies for regulations including HIPAA and GDPR. We use two-factor authentication to make sure there is no unauthorised activity on your account, and with a wealth of integrations, you can enjoy the security and convenience of SSO as well.
Share files and folders, protect them with a password or set a time limit on just how long you want them to be shared. Dropbox makes it easy for you and your team to collaborate and innovate without worrying about cyber threats or security incidents. But, if the worst should occur, you can simply recover any affected files with ease.
Security that suits you
Dropbox knows that sharing information is important. That’s why we have developed tools that let you customise your Dropbox for teams account to suit your company’s needs. The admin console lets you control features such as visibility and the Dropbox Business API lets your IT team integrate our partner products with your core processes.
Just like your team, Dropbox is also constantly assessing and improving our services to ensure your business receives only the highest standard of security, confidentiality and integrity across our services. We regularly monitor and update our testing, training, risk assessment and compliance with security policies.